Cyber Security
Let’s say a new show about the zombie apocalypse recently debuted on Netflix. All your friends are talking about how the series keeps them on the edge of their seats, and you want in on the action, only you don’t have a Netflix account.
To sign up for the streaming service, a new Netflix user would need to provide an email address, password, credit card information and a billing address. A savvy hacker will try and lure people into entering this valuable information into a fake website. Instead of signing up for Netflix, you could be sending your personal information to a hacker who can steal or sell your identity.
This is one of the many unsuspecting ways that online consumers can mistakenly pass on private information, and hackers count on uninformed internet users to be unfamiliar with the importance of cyber security. Cal Poly Pomona students are on the forefront of cyber-attack systems and methods to prevent the invasion of online privacy. Their charge is to spread awareness through their community and advance their knowledge and skills to become key players in cyber security.
Netflix and Steal
The Netflix scenario was created by students in the College of Business Administration’s Mitch Hill Center for Digital Innovations, the first student-run data center in the country.
Daneli Galan, a computer information systems student, is a co-director of the center and helped lead the Netflix demo. On one computer, you can input your personal information, and a second monitor shows how the information is easily transferred to a hacker.
“I already knew I wanted to do something with computers in high school,” says Galan, who graduated in December. “Building the actual infrastructure from the ground up, helping people program their software and being the main person to build it … it really drew me in.”
“Building the actual infrastructure from the ground up, helping people program their software and being the main person to build it — it really drew me in.”
The center allows students to design and test cloud solutions and provides an industry environment for students like Galan to translate their knowledge into applicable skills.
“I think what we’re doing at the student-run data center is what we’re going to be doing in the work field,” Galan says. “A lot of students don’t have the resources to work with the actual hardware because it’s really expensive, but we get to work with it at the center. Each team member also has different skills and we all learn from each other and help each other.”
Industry Hands-on Learning

Hacking the Competition
It’s the middle of the workday around 3 p.m., and a computer user notices the mouse arrow moving on its own. The monitor flickers, turns blue and after a computer reset, pop-up ads appear one after the other on the screen.
“That confrontation with the hackers and an online push and pull of successfully locking them out at certain points is what gets my blood pumping.”
These are signs that a computer has been hacked, signals that Cal Poly Pomona students are on the alert for to block the hacker and keep a fictitious business’ website and systems running during cyber competitions. A compromised computer means a hacker is attempting to gain access to the business’ systems. When students read the metadata, a set of data that provides information about a specific file or document, it shows an outside IP address that they can actively block to prevent the internal systems from being corrupted.
This live interaction with hackers and his attempts to successfully block them from corrupting servers excites Silas Shen.
“That confrontation with the hackers and an online push and pull of successfully locking them out at certain points is what gets my blood pumping,” Shen says. “Figuring out what exactly happened and using your knowledge to confidently say, ‘This is how they got in and this is how we’re going to stop it so they can’t get in,’ that’s another fun part.”
The computer information systems sophomore got hooked on cyber security after entering competitions in high school and being mentored by Cal Poly Pomona students and faculty through Cyber Patriot, a program that inspires K-12 students to pursue cyber security or STEM careers. He continued to enter these competitions at Cal Poly Pomona.
Phishing for Information
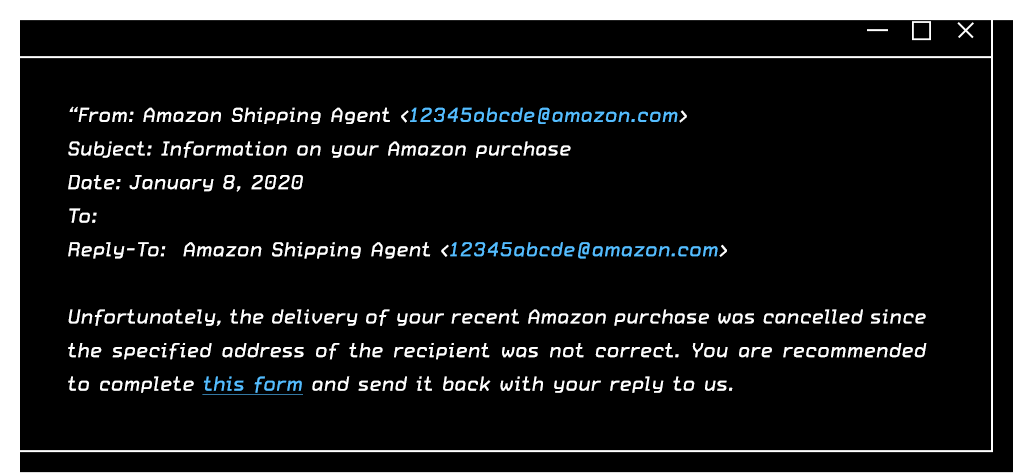
An email like this might lead an unsuspecting Amazon user to fill out the form, inputting needed information to retrieve an order. The recipient is deceived by the widely-known company name, ignores the odd email address, and possibly the fact that the user didn’t order a recent package. A hacker, who has successfully landed phishing emails into thousands of inboxes and now has access to the credit card numbers, addresses and login passwords of hundreds of customers, now has this user’s information too.
“Network attacks are the No. 1 thing that people get.”
Senior Josh Silva spent his summer researching and tagging common cyber security attacks to increase preventative measures that would stop specific attacks before they reach the user, including the above email.
“Network attacks are the No. 1 thing that people get,” says the computer engineering student. “I really had to understand what type of attacks there are and what I can do in terms of the present to prevent it. You can’t keep track of what hackers are doing because they’re always thinking of new things to do, so in terms of a hacker’s point of view, I really understood the process of what attacks happened under what specific category.”
“Since data is online, we want to make it secure.”
Silva used Zeek, a free and open source software network analysis framework, to correctly tag popular network attacks so that a system can correctly block it from coming through a specific level of the network. For instance, spam emails routinely pass through email systems and land in a user’s inbox, telling stories of princes who need help with ransom money or sending a bogus link that, when clicked, will install malware on a computer. Correctly tagging those attacks in the system will prevent the emails from entering an email inbox and leaving a user from infecting their own computer.
“People can really gather that data with their expertise, and since data is online, we want to make it secure,” Silva says. “Since cyber security is a big thing right now, my No. 1 thing is to make sure that we want a model to prevent someone from trying to get in because there’s always a process in how an attack works.”
His research data will be available to the public and can be used in future research projects and can be incorporated into programs and systems as a preventative cyber security measure.
Published February 7, 2020